What Is Cyber Essentials, Does My Business Need It?
[alert-success]What Is Cyber Essentials (Ce)[/alert-success]
Cyber Essentials is a scheme intended by the UK government to help businesses of all sizes to protect themselves against cyber-attacks. It is designed to overcome the cyber-security issues these days and to protect the sensitive information of customers, suppliers and own business. The certification process verifies a business for its current security status and ensures base-level security and key controls are taken care of.
[alert-success]Key Controls Of Cyber Essentials[/alert-success]
The scheme cliques out five security controls to defend organisations against the most communal cyber threats. Before going for Cyber Essentials certification, it is recommended to make sure your business is compliant with below factors.
[alert-announce]Secure Configuration[/alert-announce]
Secure configuration takes place at the time of building, installing and configuring the systems and network. Create a proper configuration management process or system in place to ensure consistency across all devices business users, including BYOD (Bring Your Own Device). When configuring, you need to ensure it’s executed in a way that limits weaknesses.
Weaknesses may include:
- Using default passwords crosswise systems and devices
- User accounts with redundant access privileges
- A meagre software installation method, amongst many more.
[alert-announce]Boundary Firewalls And Internet Gateways[/alert-announce]
Firewalls and gateways deliver a basic level of shield for Internet users. Firewalls monitor all the risky network traffic, identify and block unwanted traffic that can be harmful. If your firewalls are feeble and are failing to block unauthorised and known dangerous websites, your business can be exposed to threats. Encourage employees only to visit trusted, secure websites.
[alert-announce]Access Control And Administrative Privilege Management[/alert-announce]
Always make sure that right access is granted to the right user. Use the privileged identity management solution to avoid getting breached by privilege-creep. Don’t give access rights to individuals beyond what they need to do the job. Ensure all user accounts are authorised and impose a secure username and password policy, which should be regularly reviewed.
[alert-announce]Patch Management[/alert-announce]
Patch management is all about software updates. Not keeping software up-to-date can result in ransomware, brute force attempts and other cyber-attacks which come from cybercriminals’ knowledge of vulnerabilities in certain versions of the software. You can protect your business by only using licensed and supported software and installing software updates and definition updates timely. Automate the updates by scheduling or using any reputed update management solution
[alert-announce]Malware Protection[/alert-announce]
As it is pretty clear from the name, a good anti-malware software is a must for any environment. Just installing the software doesn’t help. It needs to be regularly maintained and updated. Make sure to performs regular automatic scans, scan files (particularly those downloaded from a web page) automatically for any viruses.
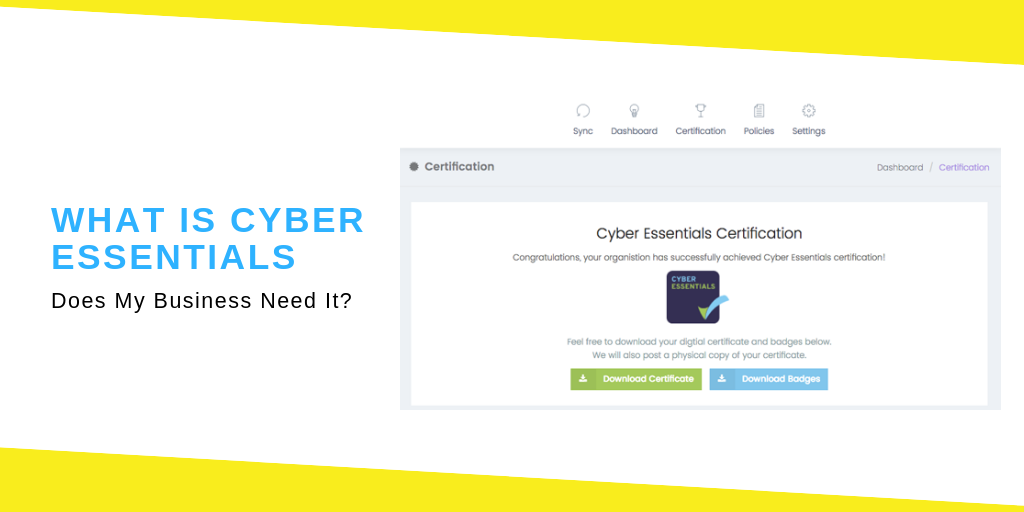
[alert-success]How Can Your Business Become Cyber Essentials Certify?[/alert-success]
Once you have completed the self-assessment, a certifying body can execute an external perimeter audit of your business to provide the assurance needed to receive the Cyber Essentials accreditation badge. There are two types of certifications available. One is ‘Cyber Essentials’, and it is a self-assessment option while the second is ‘Cyber Essentials Plus’ and is carried out by an independent certification body. Tests of the systems are passed out by an exterior certifying body, using a series of tools and techniques. Mutually Cyber Essentials and Cyber Essentials Plus must be renewed once a year.
Recommended For You
How Does An Oscilloscope Work
Most Inside
Most Inside offers high-quality recommendations and valuable updates to enhance all aspects of your life, providing premium guidance and enriching experiences.